Essential Eight Risk Assessment, Implementation & Consulting
What is Essential Eight?
In today’s digital landscape, protecting your organisation’s data and systems is more critical than ever. The Essential Eight provides a comprehensive set of strategies developed by the Australian Cyber Security Centre (ACSC). Initially designed for government entities, local councils, and public sector organisations, these strategies have become essential for private businesses looking to strengthen their cybersecurity defences.
Cyber Scope offers a solid E8 framework that serves as a starting point for improving security controls and establishing a strong cybersecurity foundation. By implementing these strategies, your organisation can effectively prevent, mitigate, and recover.
Each strategy within the Essential Eight is ranked by maturity level, allowing you to evaluate your current security posture and prioritise improvements based on your organisation’s specific needs.
Don’t wait until it’s too late. Embrace the Essential Eight to equip your organisation with advanced cybersecurity practices that protect against evolving threats. Whether you are in the public or private sector, these strategies provide a scalable solution to effectively safeguard your digital assets.
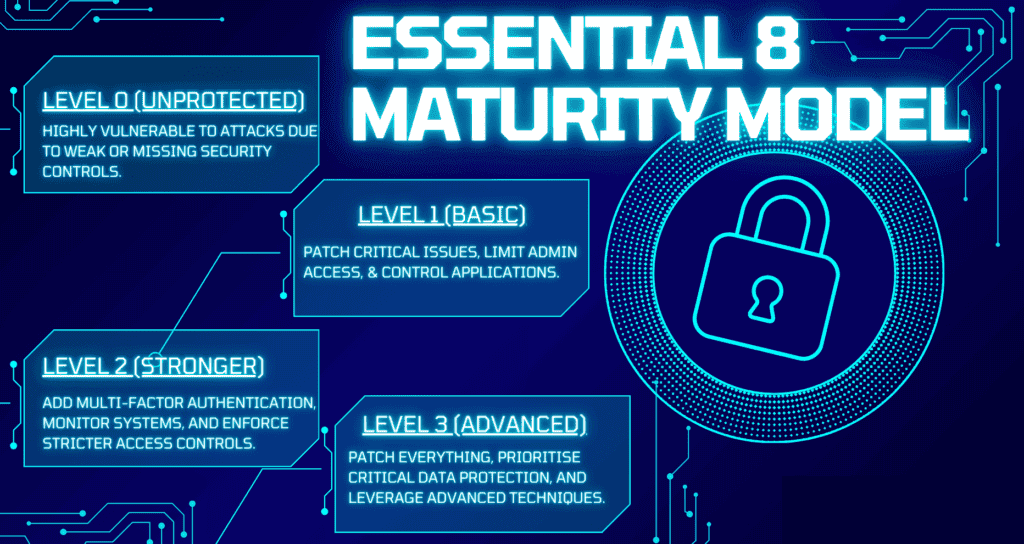
The eight strategies are divided into three primary objectives:
Objective 1: Prevent Cyberattacks
- Patch application – to remediate known security vulnerabilities
- Application control – to control the execution of unauthorized software
- User application hardening – to protect against vulnerable functionality
- Configuring MS Office Macro settings- to block untrusted macros
Objective 2: Limit the Impact of Cyberattacks
- Patch operating system vulnerabilities – to remediate known security vulnerabilities
- Restrict Administrative Privileges – to limit powerful access to systems
- Implement Multi-Factor Authentication (MFA) – to protect against unauthorized access and risky activities
Objective 3: : Data Recovery and System Availability
- Daily backups – to maintain the availability of critical data
Cyber Scope Essential Eight Maturity Uplift Is Tailored To Your Requirements And May Include:
Baseline: a current state assessment of your current controls
A baseline is established to understand and assess the current state of cybersecurity controls in your organization using the Essential 8 Maturity Model. You'll closely collaborate with Cyber Scope security experts to identify your strengths and weaknesses.
Develop a roadmap to implement the Essential 8 controls
Our team of Advisory consultants will develop a plan to bridge the gaps between your current state and the right level of maturity required for your organisation.
Assistance with executing the roadmap recommendations
After agreeing on the strategic plan, Cyber Scope's team who are top-notch cybersecurity experts, will assist in selecting the most effective risk mitigation tools and strategies and aiding in their deployment for optimal protection.
Essential 8 dashboards and audit reporting
Provide a face to face or virtual meeting to present the formal report, and help your team understand our findings and recommendations.
Continuous Reporting and Monitoring
Develop a plan to conduct regular reviews and evaluation of the effectiveness of your cybersecurity controls.
Prevent Advanced Threats
Detect and contain the most advanced threats in minutes—not hours or days—with industry-leading 24/7/365 Cyber Scope managed security services.
Please contact us for more information
