EvilProxy Phishing Kit Exploited for Targeted Account Takeover Attacks on Executives
Cybercriminals increasingly use EvilProxy phishing kit for targeted account takeover attacks, compromising thousands of Microsoft 365 user accounts, with C-level executives accounting for almost 39% of compromised users. The phishing kit exploits sophisticated techniques to bypass multi-factor authentication and is available as a subscription service, highlighting the need for enhanced security measures.
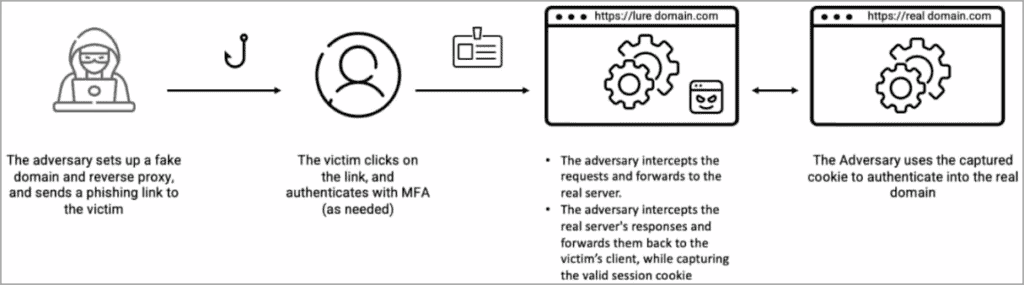
EvilProxy is a platform for phishing-as-a-service that uses reverse proxies to intercept authentication requests and user credentials between the user (target) and the legitimate service website. By proxying the legitimate login form, the phishing server can steal authentication cookies once a user logs into their account. In addition, the stolen cookie enables the threat actors to bypass multi-factor authentication since the user has already passed MFA challenges when logging into an account.
The Cyber Scope team gathered domain names and URLs associated with the EvilProxy phishing kit infrastructure. Some of these hosts were identified during post-incident response engagement with victims (companies and consumers) of online services. This information can help cybersecurity researchers and incident responders detect and attribute possible malicious activity to EvilProxy in cases involving MFA (2FA).
- 147[.]78[.]47[.]250
- 185[.]158[.]251[.]169
- 194[.]76[.]226[.]166
- msdnmail[.]net
- evilproxy[.]pro
- top-cyber[.]club
- rproxy[.]io
- login-live.rproxy[.]io
- gw1.usd0182738s80[.]click:9000
- gw2.usd0182738s80[.]click:9000
- cpanel.evilproxy[.]pro
- cpanel.pua75npooc4ekrkkppdglaleftn5mi2hxsunz5uuup6uxqmen4deepyd[.]onion
Please contact us for more information




